- Date
Privacy vs Security: A Guide to Protecting Your Data
 Andrii Romasiun
Andrii Romasiun
When people talk about privacy vs security, it's easy to get them mixed up. Here’s a simple way to think about it: Security is the fortress you build around your data, while privacy is the set of rules deciding who gets the keys and what they're allowed to do once inside.
One is about stopping bad actors from getting in. The other is about governing what the good guys can do with the access they have. They are deeply connected, but they tackle different parts of the data protection puzzle.
Defining Privacy and Security in a Digital World
In any discussion about data, you'll hear "privacy" and "security" thrown around, often as if they mean the same thing. They don't. Nailing down the difference is the first real step toward creating a data strategy that's both strong and ethical. Security is your technical backbone, but privacy provides the ethical and legal guardrails.
The Core Distinction
Security is all about shielding data from threats. It's the collection of technical measures you put in place to stop people from accessing, using, changing, or destroying information they shouldn't. Think of it as the locks on your doors, the firewall protecting your network, and the encryption scrambling your files. It’s the practice of defending information.
Privacy, on the other hand, is about a person's right to control their own information. It deals with how data is collected, used, and shared, even by organizations that have permission to access it. For example, a social media platform might have top-notch security to keep your account safe from hackers, but its privacy policies dictate how it can use your personal data for advertising. This often involves tracking user behavior with things like cookies, a topic you can dive into by reading everything you need to know about cookies.
A Side-by-Side Comparison
This infographic does a great job of visualizing the distinct, yet related, roles that privacy and security play.
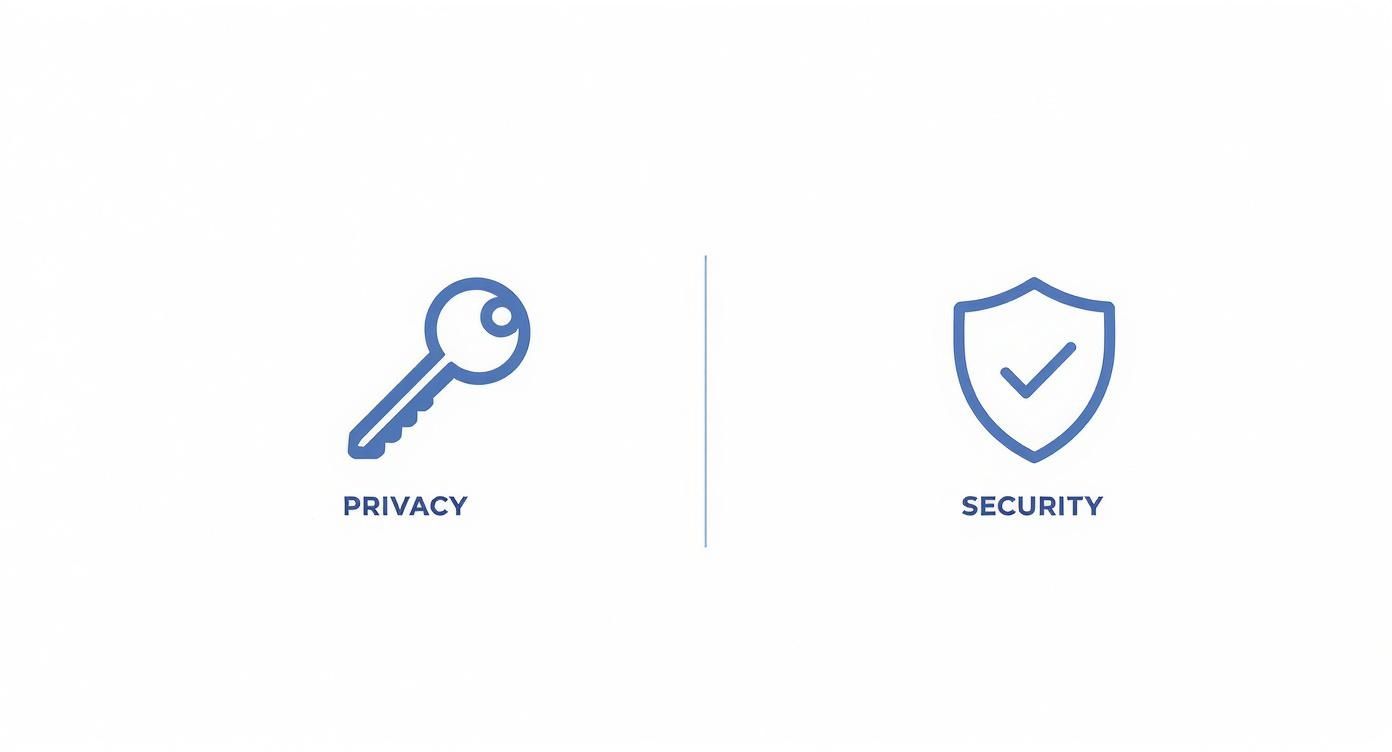
As you can see, security is the technical defense—the shield. Privacy is more about control and rights—the key.
This isn't just a semantic difference; it's reflected in major global trends. Spending on security and risk management is on track to hit $212 billion by 2025, which is a 15% jump from the year before. At the same time, a staggering 92% of Americans are worried about their online privacy. This has pushed governments and businesses to tighten data laws and invest in new privacy-enhancing technologies.
To make the distinction crystal clear, here’s a quick table breaking down the core differences.
Quick Comparison: Privacy vs. Security
This table sums up the fundamental differences between data privacy and data security across a few key attributes.
| Attribute | Data Privacy | Data Security |
|---|---|---|
| Primary Goal | To empower individuals with control over their personal data and define how it is used. | To protect data from unauthorized access, breaches, and cyber threats. |
| Focus | Defines who can access data and for what purpose (Policy-driven). | Prevents unauthorized access and ensures data integrity (Technology-driven). |
| Key Question | "Should we be collecting this data, and how are we going to use it?" | "How can we stop this data from being stolen or compromised?" |
While they approach the problem from different angles, you can't have true privacy without solid security in place to back it up.
How Strong Security Can Conflict with Personal Privacy
It's easy to assume security and privacy are two sides of the same coin, but their relationship is often more adversarial. While security is absolutely necessary to protect your privacy, an aggressive, all-out push for security can sometimes steamroll personal privacy altogether. This fundamental tension pops up when security tools demand extensive data collection or monitoring just to do their job.
This isn't just some abstract concept; it's a conflict we see play out every single day. Think about it: strong security often tries to make an environment completely transparent so that threats can be spotted and dealt with instantly. Privacy, on the other hand, is all about creating a bit of opacity—giving people control over who gets to see their information. The friction starts right there, at the intersection of transparency for security and opacity for privacy.

When Security Measures Intrude on Privacy
Take workplace surveillance, for example. A company might install heavy-duty security protocols to guard its intellectual property. These measures often include monitoring employee emails, tracking every website visited, or even logging keystrokes on company computers. From a strict security perspective, these are perfectly logical moves to stop insider threats.
But from a privacy angle, it’s a massive intrusion. This kind of monitoring can easily pick up personal chats, private health details, or financial data, completely erasing the line between professional and personal life. In this scenario, the company's data security is bought at the cost of employee privacy.
We see a similar trade-off in national security debates. Governments often argue that mass surveillance programs are critical for stopping terrorist attacks. To keep the country "secure," they might scoop up phone records, internet histories, and location data from millions of people, all without a warrant. While this might bolster the state's security framework, it guts the privacy of the general public.
The Encryption Backdoor Debate
Perhaps the most classic example of the privacy vs. security conflict is the never-ending debate over encryption backdoors. Law enforcement agencies frequently demand special access to encrypted communications, arguing it's essential for solving crimes and keeping people safe. Their solution? Forcing tech companies to build a "backdoor" into their encryption that only officials can use.
Security experts and privacy advocates are almost universally against this, and for good reason:
- A backdoor for one is a backdoor for all: Creating a "master key" for law enforcement also creates a glaring vulnerability that criminals and hostile governments would be dying to exploit. You simply can't guarantee it wouldn't fall into the wrong hands.
- It undermines trust: The whole point of end-to-end encryption is that only the sender and receiver can read the message. A backdoor shatters that promise, destroying user trust in supposedly secure platforms.
- It creates a slippery slope: If access is granted for one type of serious crime, it sets a precedent. Soon, there could be demands for access in less severe cases, leading to a slow but steady expansion of surveillance powers.
"Security without privacy is surveillance. It creates a system where data is protected from outsiders but completely exposed to those in control, removing individual autonomy and freedom."
This quote nails it. When security measures wipe out private spaces, the result isn't protection—it's control. The real goal should be to design systems where security and privacy actually support each other.
Finding a Balanced Approach
Striking that balance isn't easy; it requires a conscious and careful design philosophy. Instead of hoarding as much data as possible "just in case," organizations should embrace data minimization. This means collecting only the data that is absolutely necessary for a specific, defined purpose and nothing more.
This is where the distinction becomes critical. Real digital protection doesn't just lock the doors; it respects the people living inside. It understands that privacy isn't about hiding secrets, but about having the freedom to choose what you share.
Ultimately, privacy without security is just a nice idea—unprotected data is a free-for-all. But security without privacy is a gilded cage: you might be safe, but you're not free.
What a Data Breach Teaches Us
There's no better, or more painful, way to understand the link between privacy and security than to look at what happens after a major data breach. Suddenly, the abstract debate becomes a real-world crisis, showing how one security lapse can trigger a privacy catastrophe for millions. It’s like watching dominoes fall, starting with just one weak link.
A breach usually starts small. Maybe it's an employee with a weak password, a server that missed a software patch, or a convincing phishing email that tricks someone into handing over their credentials. From a purely security perspective, the initial failure is the unauthorized access itself. The walls have been breached.
But the real damage is just getting started. This is the exact moment a security problem morphs into a full-blown privacy disaster.
The Journey From Exploit to Exposure
Once attackers get inside, they aren't there to look around—they're there to steal. This is the data exfiltration phase, where they copy and pull sensitive personal information out of its supposedly secure environment. We're talking names, email addresses, home addresses, financial details, and sometimes even health records.
From there, the stolen information often ends up for sale on the dark web or is just dumped publicly, leading to devastating privacy violations for every person on that list. The failure to secure the data directly caused the loss of control over that personal information—which is the textbook definition of a privacy failure.
The aftermath unfolds in a few predictable, and painful, stages for everyone involved.
For Individuals: The consequences are immediate and deeply personal. Victims are thrown into a world of heightened risk, facing identity theft, financial fraud, and sophisticated phishing attacks. Their private information is now a commodity for criminals, and that sense of personal safety is gone.
For Organizations: The fallout is a multi-front war. Beyond the eye-watering costs to fix the technical issues, companies bleed customers, lose trust, face massive regulatory fines, and get buried in lawsuits.
A data breach teaches one lesson loud and clear: security is the system that enforces your privacy promises. When security breaks, those promises are shattered, and so is the trust your users placed in you.
The Staggering Financial and Human Cost
The numbers behind data breaches are staggering and climbing every year, making it impossible to ignore the connection between security spending and privacy protection. The problem is getting worse globally. The Identity Theft Resource Center tracked 1,732 publicly disclosed data breaches in just the first half of 2025—a 5% increase from the same time in 2024. Projections show cybercrime could cost businesses a mind-boggling $10.5 trillion by the end of 2025. As these figures from various cybersecurity statistics show, security failures don't just cost money; they directly lead to massive privacy losses.
This financial pressure forces a hard look at priorities. Investing in security is no longer just an IT line item; it's a core business function dedicated to protecting customers and ensuring the company can even stay afloat. In fact, companies that use strong security measures, like AI and automation, can slash the average cost of a breach by nearly 40%.
But the cost isn't just about dollars and cents. For any business built on user data, trust is the entire foundation. A data breach sends a clear message to customers: "We can't keep your information safe." That's an existential threat. This is why more organizations are adopting a "privacy by design" mindset. By exploring options like self-hosted web analytics, they're building a commitment to both security and privacy right into their operations, which is one of the few ways to start rebuilding that broken trust.
In the end, a data breach is a harsh teacher. It proves, without a doubt, that privacy and security aren't two separate goals. They are two sides of the same coin, both essential for responsible data stewardship. If you let one fail, the other is sure to follow, leaving a trail of financial ruin and human impact behind.
How AI and Encryption Are Changing the Game
The relationship between privacy and security is being completely reshaped, and new technologies are at the heart of this transformation. Artificial intelligence and advanced encryption, in particular, are a double-edged sword. On one side, they offer incredible new tools for protecting our data; on the other, they introduce powerful new methods for surveillance and control.
AI, for instance, has become a massive asset for cybersecurity teams. Machine learning algorithms can watch network traffic in real-time, spotting the faint signals of a breach long before a human analyst ever could. This kind of proactive threat detection makes systems more secure, which in turn helps protect the privacy of the data locked inside.
But there's a flip side. The very same AI that's great at spotting threats can also be turned into a potent surveillance tool. AI-powered systems can churn through enormous datasets to track behavior, predict what people might do, and identify individuals—often without them even knowing. This is where the pursuit of security starts to look like a society under constant digital watch, creating a huge privacy problem.
The Rise of Privacy-Enhancing Technologies
In response to these worries, a new category of tools called Privacy-Enhancing Technologies (PETs) has started to gain traction. PETs aren't just about building higher walls around data; they’re about fundamentally minimizing how much personal data gets exposed in the first place. This allows companies to get the insights they need from data without having to compromise the privacy of the people behind it.
This chart from Wikipedia gives a great overview of the different types of PETs, showing the various strategies used to keep data safe while it's being analyzed.

The big idea here is that PETs act as a bridge, connecting the often-competing demands for useful data and personal privacy.
And their adoption is picking up speed. Some experts predict that by the end of 2025, 60% of large organizations will be using these techniques to analyze data without exposing raw personal information. This shift shows a clear trend: we're increasingly looking for technological solutions to balance security needs with privacy rights. You can read more about what to expect in global privacy from fpf.org.
Decentralization and User Control
Beyond PETs, the push for more privacy is also sparking new ideas about who should own and control data. The concept of decentralized identity is a fantastic example. Instead of letting a few giant tech companies manage our digital lives, this model gives individuals the keys to their own credentials.
Using technologies like blockchain, you could hold your own identity information and grant specific, temporary access to services when you need to. This completely flips the power dynamic, putting control back in the hands of the individual, not the corporation.
Decentralization fundamentally changes the data relationship. It moves from a model of "trust us with your data" to "prove you need this data," giving users direct control over their digital footprint.
This new approach offers a much better way forward:
- Minimized Data Sharing: Users only share the absolute minimum information needed for a specific interaction, not their entire life story.
- Revocable Consent: Access isn't a one-time decision. You can grant it and take it away in real-time.
- Enhanced Security: With no massive, central database of personal info, the risk of a catastrophic data breach that affects millions is dramatically lower.
As AI gets woven deeper into our daily lives, these kinds of technological and structural changes will be essential. They represent a deliberate effort to design systems that don't force us into a false choice between privacy and security. Instead, they aim to build security in a way that respects and protects our privacy from the start.
Choosing Privacy-First Web Analytics Tools
The whole privacy vs. security debate gets very real when you're picking tools for your business, especially for web analytics. For a long time, the standard playbook was to grab as much user data as possible, sacrificing privacy for what seemed like better insights. But that's changing. A new wave of tools is proving you can have both.
You can absolutely get powerful, useful data without snooping on your visitors. This isn't just about doing the right thing, either—it's smart business. With data laws like GDPR and CCPA getting stricter, switching to privacy-first analytics is essential for staying compliant and earning trust.
Shifting From Data Harvesting to Privacy by Design
Let's be honest, traditional analytics platforms were built to collect everything. They use cookies and other trackers to piece together detailed profiles of individual people, and that data often gets shared or sold. This model is a privacy minefield and puts all the compliance stress right on your shoulders.
Privacy-first analytics completely flips that script. Instead of following individuals around the web, these tools focus on aggregated, anonymous data to show you the big picture. They’re built from the ground up to give you the insights you need—top pages, where traffic is coming from, conversion funnels—without ever touching personally identifiable information (PII).
This “privacy by design” philosophy means compliance isn’t something you bolt on at the end; it's baked right into the platform. If you're looking to dive deeper into selecting the right tool, our guide on finding effective privacy-friendly analytics is a great place to start.
Comparing Analytics Philosophies
When you get down to it, the differences between these two approaches are night and day. One is all about granular, individual tracking, while the other is about anonymous, high-level insights that don't require begging for consent. The real split is about what data is collected and, crucially, who owns it.
A privacy-first tool operates on the principle of data minimization. It asks, "What's the least amount of data we need to be useful?" instead of, "How much data can we possibly grab?"
Take a look at this dashboard from Swetrix. It’s a perfect example of how you can display all the essential metrics without any invasive tracking.
You can see key indicators like unique visitors, page views, and bounce rate at a glance. No cookies or fingerprinting required.
To make the differences even clearer, let's break down the core philosophies behind these two models in a table.
Web Analytics Approaches: Traditional vs. Privacy-First
This table compares the fundamental differences between old-school, data-heavy analytics and modern, privacy-respecting solutions.
| Feature | Traditional Analytics (e.g., Google Analytics) | Privacy-First Analytics (e.g., Swetrix) |
|---|---|---|
| Data Collection | Gathers extensive user-level data, including demographics, interests, and cross-site behavior using persistent cookies. | Collects anonymous, aggregated data. Avoids cookies and fingerprinting to prevent individual user tracking. |
| Data Ownership | Data is often processed and owned by the platform, potentially used for their own business purposes (e.g., ad targeting). | You retain 100% ownership of your data. It is never shared, sold, or used for any other purpose. |
| Compliance | Requires complex configuration, cookie consent banners, and careful policy management to comply with GDPR, CCPA, etc. | Compliant by default. No cookie banner is needed because no personal data is collected or stored. |
| User Experience | Relies on intrusive consent banners that can disrupt the user journey and lead to higher bounce rates. | Provides a seamless user experience with no pop-ups, as tracking is non-invasive and anonymous. |
Ultimately, choosing a privacy-first tool is how you put the balance of security and privacy into practice. You secure your analytics while respecting your users' privacy, turning a potential headache into a real competitive advantage.
Taking Action: Practical Ways to Protect Your Digital Footprint
Knowing the difference between privacy and security is one thing, but putting that knowledge to work is what really counts. Whether you're a business owner or just managing your own digital life, a few deliberate steps can seriously beef up your defenses. It’s all about building habits that respect both sides of the coin.
For businesses, this is about more than just checking compliance boxes; it’s about creating a culture that genuinely values data stewardship. For the rest of us, it’s about getting smarter with our online habits to limit our exposure in a world that’s always asking for more of our information.
For Businesses: Earning Trust and Ensuring Compliance
Companies hold a massive responsibility to protect the data they handle. A solid strategy isn't just about dodging fines—it's about building real customer loyalty and a brand people trust. If you're looking for where to start, focus on these three high-impact areas:
- Embrace Data Minimization: The golden rule: if you don’t absolutely need it to run your service, don’t collect it. Get into the habit of regularly purging data that’s no longer essential. Less data means less risk.
- Run Privacy Impact Assessments (PIAs): Before you roll out a new product or feature, take the time to systematically assess how it might affect user privacy. This simple, proactive step helps you spot and fix risks before they turn into full-blown problems.
- Build a Security-First Culture: Security is a team sport. Train everyone—not just the IT department—on best practices, from spotting a phishing email to using strong, unique passwords.
For Individuals: Taking Back Control of Your Data
You have more power here than you might think. Small, consistent changes to your routine can dramatically improve your privacy and security, making you a much tougher target for both trackers and attackers.
Protecting your digital footprint isn't about going off the grid. It's about making conscious choices about what you share, who you share it with, and how that information is secured.
Here are a few essential habits to get you started:
- Get a Password Manager: Seriously, stop reusing passwords. A good password manager will create and remember ridiculously strong, unique passwords for every single one of your accounts. It's one of the easiest, most effective security upgrades you can make.
- Turn On Multi-Factor Authentication (MFA): For your critical accounts—think email, banking, social media—MFA adds a crucial second layer of defense. Even if a thief manages to steal your password, MFA will stop them in their tracks.
- Be Stingy with App Permissions: When you install a new app, pay close attention to what it's asking for. Does that flashlight app really need access to your contacts and location? If a permission seems excessive, just say no.
Frequently Asked Questions About Privacy and Security
https://www.youtube.com/embed/ZBOX_MDtMic
Digging into the privacy vs security debate often brings up more questions than answers. Let's tackle some of the most common ones to clear up the confusion and highlight how these two concepts really work together.
Can You Have Security Without Privacy?
Absolutely, but it’s not a world you’d want to live in. A system can be perfectly secure against outside attackers while offering zero privacy to the people using it. Think of it as a fortress with guards watching every move you make inside.
A classic example is a corporate network that tracks every email, message, and file you touch. It’s incredibly secure from hackers, but it offers no personal privacy for employees. The goal isn't just to lock the doors; it's to build a secure space where privacy is respected and protected, not eliminated.
Which Is More Important: Privacy or Security?
This is like asking what’s more important: a foundation or the house built on top of it. They are completely dependent on each other, and their importance shifts with the situation. Security is the essential foundation—without it, any promise of privacy is just empty words, easily broken by the first breach.
But security doesn't exist in a vacuum. Its whole purpose is often to protect privacy. Consider a hospital’s database. The technical measures used to secure patient data (security) exist to uphold patient confidentiality (privacy). The best approach is to build a strong security framework designed from the ground up to achieve specific privacy goals.
The most effective systems don't treat privacy and security as competing interests. Instead, they view strong security as the essential tool required to deliver on their privacy commitments to users. This synergy builds trust and resilience.
How Do Privacy Laws Like GDPR Affect Security?
Privacy laws like the GDPR and CCPA have completely changed the game for security. They don't just recommend security; they legally require it. These regulations turn security from a smart business practice into a non-negotiable legal obligation for anyone handling personal data.
A core concept in these laws is 'security by design and by default.' This isn't just a suggestion; it's a mandate. It means companies must build security and data protection into the very fabric of their systems from day one, not tack it on as an afterthought.
This legal pressure has led to some massive improvements, ensuring that:
- Security is baked into projects from the very start.
- Data protection becomes an ongoing, documented part of operations.
- Companies are held legally and financially accountable when security failures lead to privacy breaches.
In short, privacy legislation has become one of the biggest drivers for better, more robust security practices across every industry.
Ready to get actionable insights without compromising user privacy? Swetrix offers powerful, cookie-free web analytics that are GDPR-compliant by design. Start your 14-day free trial and see how easy it is to grow your business ethically. Learn more and sign up today at swetrix.com.